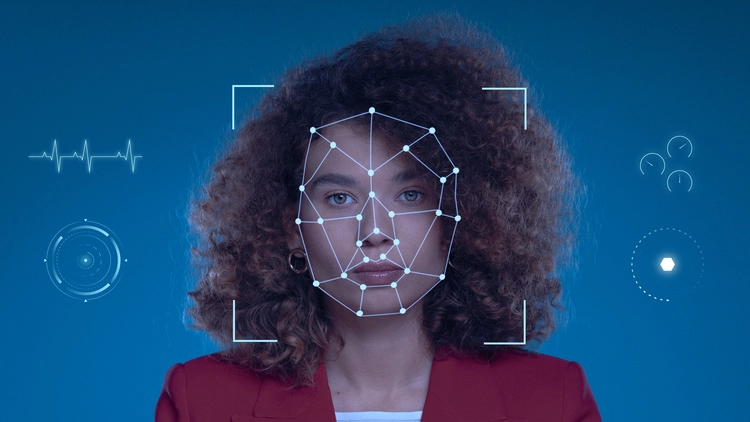
Computer Image Verification and Authentication
The process of checking and authenticating photographs using computer algorithms and techniques is known as computer image verification and authentication.

Computer picture authentication and verification are crucial in the current digital era for protecting private data and thwarting fraud. The technologies used for computer image verification and authentication, as well as their various uses, are thoroughly discussed in this article.
What is Computer Image Verification and Authentication?
The method of computer image verification and authentication involves using photographs to confirm someone’s identification. In order to confirm the authenticity of the person or object in the photograph, computer algorithms are used to examine and verify the distinctive qualities of an image, such as its shape, size, colour, and texture.
How Does It Work?
The following steps are involved in computer picture verification and authentication:
1. Image Acquisition
Image acquisition is the initial step in the verification and authenticity of images. It entails taking a picture of the individual or thing that needs to be validated. Using a scanner or a digital camera, the image can be taken.
2. Image Processing
Following capture, computer algorithms are used to process the image. The algorithms use an analysis of the image’s edges, lines, forms, and colours to produce a distinctive digital signature.
3. Image Comparison
Image comparison comes next. To verify the authenticity of the taken image, the digital signature is compared to a database of digital signatures that already exist. The image is regarded as authentic if the digital signature matches any signature in the database.
4. Authentication Decision
The decision regarding authentication is taken in light of the outcomes of the image comparison. The person or thing in the photograph is taken to be authentic if the digital signature matches any other signature in the database. If not, the image is disregarded as fake.
Applications of Computer Image Verification and Authentication
Computer image verification and authentication have several applications, including:
1. Access Control
Access control is one of the most often used applications for computer image verification and authentication. It is used to confirm someone’s identification in order to provide or prohibit access to a secure space, like a building, workplace, or computer network.
2. Online Transactions
Online transactions are another area where computer image verification and authentication are used. It is used to verify the identification of consumers engaging in online transactions including social media, e-commerce, and online banking.
3. Border Control
In order to verify the identity of people crossing international borders, border control also uses computer image verification and authentication. It aids in the prevention of illegal immigration and identity theft.
Advantages of Computer Image Verification and Authentication

Compared to more established authentication techniques, computer image verification and authentication offer the following benefits:
1. High Security
High security is provided by computer picture verification and authentication since it is challenging to copy or fake an image. Additionally, because it doesn’t involve making physical contact with the subject, it offers a non-intrusive method of identity authentication.
2. Convenience
It is convenient to utilise computer image verification and authentication because it eliminates the need for the user to carry physical tokens or remember passwords. It is also quick because it only takes a few seconds to confirm someone’s identification.
3. Cost-Effective
The cost-effectiveness of computer image verification and authentication is due to the lack of expensive hardware or software requirements. Additionally, it is simple to incorporate into already-in-use authentication systems..
Types of Image Verification and Authentication
Important methods for assuring the validity and integrity of digital photographs include image verification and authentication. Several different kinds of image verification and authentication methods exist, such as:
- Metadata analysis: Metadata is information that is stored as part of an image file and includes details like the date and time the image was taken, the camera model, and the place where it was taken. Analysing the metadata entails looking over this data to confirm the validity of the image.
- Image hashing: A method called image hashing creates a distinct digital fingerprint for each image. This fingerprint can be used to confirm the image’s validity because any changes to the image will change the hash value.
- Watermarking: An image can be authenticated by adding a visible or invisible mark, known as watermarking. While invisible watermarks are embedded within the image data, visible watermarks may take the form of logos or text overlays.
- Forensic analysis: In forensic analysis, an image is carefully examined to look for any indications of tampering or alteration. This may entail looking for any anomalies or inconsistencies by inspecting the image’s pixel data, compression, and file structure.
- Blockchain verification: By generating a tamper-proof record of the creation and ownership of digital images, blockchain technology can be used to confirm their legitimacy. The legitimacy of photos used in legal or financial contexts can be confirmed using this.
The best strategy will depend on the particular use case and context. Each of these techniques has advantages and disadvantages of its own.
Future of Image Verification and Authentication
With the development of technology and the emergence of new applications, the field of picture verification and authentication is expanding quickly. The following are a few probable future developments and uses:

- Improved AI-based techniques: Deep learning and machine learning methods have showed promise in improving picture authentication and spotting image manipulation. These methods might grow even better at spotting complex image alteration as they advance.
- Multi-modal authentication: Utilising multiple authentication methods, such as combining metadata analysis with watermarking or image hashing, is known as multi-modal authentication. In comparison to using just one technique, this can offer a stronger and more dependable authentication system.
- Authentication for augmented reality (AR) and virtual reality (VR): There will be a greater need for digital content authentication and verification as AR and VR are used more often across a range of businesses. In this situation, methods like blockchain verification may be quite helpful.
- Authentication for deep fakes: Image authentication is severely hampered by deep fake technology, which entails producing incredibly convincing fake images and movies. To identify and stop deepfakes from being utilized to disseminate false information or carry out malicious operations, new methods and strategies are required.
- Integration with Internet of Things (IoT) devices: Image authentication may become more integrated with IoT devices as they grow more widespread. To verify the accuracy of the images they record, IoT devices with cameras may need authentication.
In general, advances in AI, multi-modal authentication, and the advent of new applications and technologies are expected to affect the future of picture verification and authentication. The security and dependability of digital photographs will be enhanced by these improvements, which is crucial in the digital era.
Conclusion
In conclusion, using computer image verification and authentication is a highly effective way to protect sensitive data and stop fraud. In order to confirm the authenticity of the person or object in the image, it employs cutting-edge computer algorithms to analyse and verify the distinctive qualities of an image, such as its shape, size, colour, and texture. Computer image verification and authentication is becoming more and more common in a variety of fields and applications due to its high security, practicality, and affordability. We can anticipate more developments in this area as technology develops, making it an even more crucial instrument for data protection.